Supply chain attacks
This note provides an overview of “supply chain attacks” and presents how this attacking technique is related to known cyber-threats.
- Published
- August 29, 2017
Introduction
The recent NotPetya outbreak, the compromise of eight Chrome-browser extensions as well as the compromise of a popular server management software are all distinct cyber-attacks that used the same attacking technique, which is known as “supply chain attack”. This note provides an overview of “supply chain attacks” and presents how this attacking technique is related to known cyber-threats.
Background information and recent attacks
In a nutshell, a “supply chain attack” refers to the compromise of a particular asset, e.g. a software provider’s infrastructure and commercial software, with the aim to indirectly damage a certain target or targets, e.g. the software provider’s clients. This type of attack is typically used as a first step out of a series of attacks. More concisely, it is used as a stepping stone for further exploitation, once foothold is gained to the target system or systems.
Recent cases of “supply chain attacks” are the following:
- NotPetya. The “NotPetya” malware spread to systems that had a specific accounting software installed. The investigation of the incident revealed that the threat actor behind the attack compromised the infrastructure of the software provider, tampered the software, and pushed the tampered version of the software to the provider’s clients as a legitimate software update. The software update essentially installed the “NotPetya” malware on the victim-machines.
- Chrome extensions compromised. As recently reported, a series of Chrome browser extensions were compromised through phishing attacks targeting the developers of those extensions. The compromised extensions were leveraged in order to manipulate internet traffic and to serve malicious advertisements to all systems that had them installed. Moreover, the malicious extensions aimed at stealing CloudFlare credentials from the victim machines.
- ShadowPad backdoor. A backdoor dubbed ShadowPad was injected into a network management software suite and was pushed through a software update to the respective systems that had the software installed. The attack was spotted when a company using the software observed suspicious domain name lookup requests. Such a backdoor could potentially allow the threat actor behind the attack to load malware on the victim systems and/or exfiltrate data.
Cyber-threat context in supply chain attacks & recommendations
Supply chain attacks may involve different types of cyber-threats. The figure below uses the security incident of the compromised Chrome extensions as a use-case and presents the steps involved in the attack. This supply chain attack involves threat types that have been described in ENISA’s Threat Landscape (Phishing, Identity Theft, Web application attacks, Web based attacks).
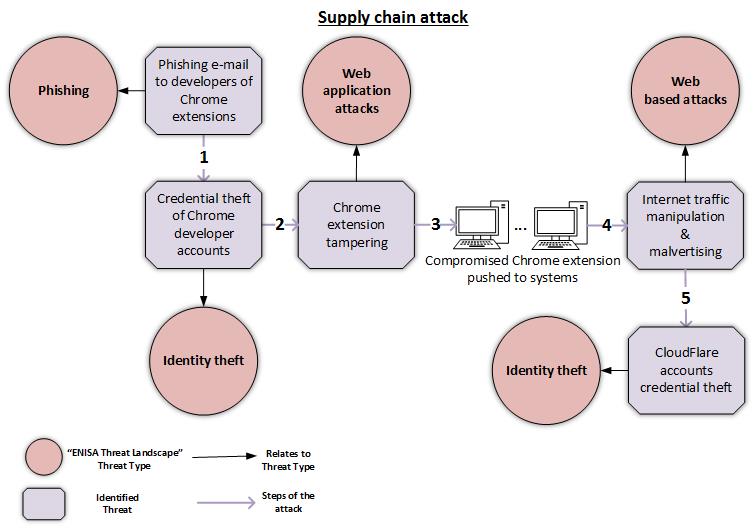
Identifying the cyber-threats involved in this supply chain attack, provides a reference point to ENISA’s Threat Landscape for more security recommendations. Indicative recommendations for the compromised Chrome extensions chain supply attack, are the following:
- Phishing. End-users should use two-factor authentication whenever possible. Companies should raise awareness regarding elaborate phishing campaigns through proper training.
- Identity Theft. Users should use long, complex, unique and secure passwords as well as two-factor authentication whenever possible.
- Web application attacks. Disable software, e.g. browser extensions, that is not actively used or needed.
- Web based attacks. Keep the operating system and installed software updated as soon as new updates are available.
Conclusion
In the aforementioned supply chain attacks, it is evident that the software that was compromised provided a significant attack surface to the threat actors. Supply chain attacks are quite alarming since the compromised software essentially poses a single point of failure for the security of several entities that do nothing more than installing and updating trusted software. Supply chain attacks are quite effective and severe since they enable threat actors to indirectly damage their targets and allow them to reach several systems at once. Concluding, best practices should be followed at all times, e.g. the use of two factor authentication, since they constitute the fundamentals of cyber-security (on which robust security should be built upon), and they can often stop an attack at its very beginning.